Email spoofing Hacking class 21
Email spoofing Hacking class 21
Hi friends, After the article about SMS spoofing, today i will share with you basic idea about What is email Spoofing? How email spoofing works? What are the different ways to send spoofed emails? Can we detect spoofed emails or not? In my later hacking class tutorials i will explain you how to send spoofed emails using email spoofing tools or by simply web applications. So Let’s start from very basic..
What is Email Spoofing?
Email spoofing refers to the process of sending an email message from one source, but making it appear as though the email was sent from a different source. For example, an email originates from user@domain.com but it appears to be from email@address.com. Another method of spoofing is to make the message appear to come from an unknown user within your domain name. For example, the message appears to be from support@yourdomain.com.
This does not mean that your email account was compromised. It means that the sender has fooled the mail client into believing the email originated from a different address.
This is usually done for malicious reasons, either to distribute unsolicited email or to distribute email viruses. Unfortunately, there is no real way to prevent spoofing from occurring. If you receive an email that has questionable content, it is recommended to delete the email message or use an antivirus program to scan the message before opening it.
This does not mean that your email account was compromised. It means that the sender has fooled the mail client into believing the email originated from a different address.
This is usually done for malicious reasons, either to distribute unsolicited email or to distribute email viruses. Unfortunately, there is no real way to prevent spoofing from occurring. If you receive an email that has questionable content, it is recommended to delete the email message or use an antivirus program to scan the message before opening it.
I will recommend users to read the following article to know about How email works:
How Email Works tutorial
How Does Email Spoofing Work?
Basically, email spoofing alters the email header to make it appear as though it originated from a different source address. This is possible due to the simple mail transfer protocol (SMTP) not supporting any type of sending authentication. Originally, email spoofing was used for legitimate reasons when someone wanted to send mail appearing to be from their email address when logged on to a network that was not their own. Nowadays, it is commonly used for sending spam or malicious mails means for sending viruses or phishing page links or simply spreading the botnets. The email fields can be edited in many email clients and automated spam and hacker tool kits that are currently available in the market or you can also also edit them manually if you know little bit of programming and hacking.
Why do People Spoof Email?
Email is primarily spoofed for one of two basic reasons:
1 – Spam means for Email marketing or spreading a message to several users.
2 – To conduct a phishing or spear phishing attack.
If you want to learn more about phishing then i will recommend you to read this article:
How to hack Gmail accounts step by step
Spammers will spoof the “from” field many times in order to hide their identity from the email recipients. The message body will have advertisements, or links to offers the spammers are trying to sell to the recipients. They change the “From” field in the email in order to make it harder to determine their identity and avoid complaints from the end-user.
Those who spoof email for malicious intent are simply called Crackers and they typically do so as part of a phishing attack that is for sending phishing page links. They will spoof the email to be from someone else on the same domain as the receiver. In a spear phishing attack, the email may be changed to be from a legitimate friend or co-worker of the person receiving the email. This results in a greater possibility of the targeted person opening the email and falling victim to malware or spyware attack.
What are the Techniques to Spoof Email?
Although it is straight forward to change the “From” field in an email header, the email can still be traced to the sender. But most of the major ISP’s maintain “black lists” to ban known senders of spam from sending email traffic to users on their network(s). As a result, spammers have now evolved to using specialized software to create a random sending email address. These email addresses will rarely be active or used for a second time.
Another technique used by those conducting spear phishing attacks is to hack the account password(s) for one or more people in the organization or some normal victim. Once its hacked, the emails in the address book are used to conduct additional attacks by placing those in the “From” field in email making them to appear to be legitimate. This same technique is also used by email worms(botnets) to self-propagate through unsuspecting users opening infected email sent by the respective worm.
Can Spoofed Emails be Detected?
Now a major question arises that can we trace such activities that is email spoofing. Answer is simply no if user is smart enough that is he has used a proxy server while sending the spoofed email and answer is Yes if a novice hacker has send it without spoofing his IP address.
I would recommend you to read this article to hide your IP and remain anonymous while sending emails and performing such hacking activites:
How to Hide your Privacy Online using Super Hide IP.
Many people mistakenly believe that sending spoofed email The IP address used to send an email is logged and is traceable. This address can then be used to cross-reference with the ISP DHCP records to determine who sent the email. If you are simply trying to trick your sibling or friends, it will appear to be from the “faked” email address. This is why spammers and hackers will not send spoofed email from their own IP address(es), instead routing the spam through other destinations before sending it to the desired recipients.
If you want to learn more about How to trace an email address that you have send you the email and from which IP address the read the following article:
How to trace an Email Address and original sender?
That’s all the tutorial, i hope you all have like it. If you liked it then show your love by posting comments about the article.
IF YOU HAVE ANY QUERIES ASK ME..
This Tutorials Is Only For Educational Purpose If Misused i am Not Responsible.

1. Are You Being Blackmailed or Threatened through e-mail for large amount of money?
2. Are your employees, partners or alliances receiving foul e-mails that are hampering your day-to-day business activities?
Most modern days Internet Users use standard e-mail clients (Like Outlook Express, Microsoft Outlook, Eudora Pro, Opera Etc.) to send and receive e-mail messages on the Internet. Such e-mail clients are not only very quick and easy to use, but also provide users with a variety of useful features.E-mail clients make it very easy for one to turn a blind eye to the inner working of e-mails systems. However, understanding how e-mail system work is extremely important if one actually wants to be able to solve email related threats.
It is extremely important for Internet Users To Understand How E-mails travel on the Internet. Unless one becomes familiar with the working of e-mail systems, it is impossible to counter such threats.
All Email Communication on the Internet Is Governed by rules and regulations laid by two different Protocols:-
Simple Mail Transfer Protocol (SMTP Port 25)
Post Office Protocol (POP Port 110).
Basically, The e-mail system is quite analogous to that of snail mail. Each time an e-mail has to be sent, the sender connects to a local mail server (Post Office) and uses predefined SMTP Commands to create and send the email. This local mail server then uses the SMTP protocol to route the E-mail through several other interim mail servers, until the e-mail Finally reaches the destination mail server (Post Office). The recipient of the E-mail Then Connects to Destination post office server to download the received e-mail using predefined POP Commands.
The SMTP (Simple Mail Transfer Protocol) is used to send e-mails, while the POP protocol is used to receive them.
To recapitulate, each e-mail on the internet originates at the sender post office server (With the help of SMTP Commands), is routed via a number of interim mail servers and then finally reaches the destination post office where the receiver uses POP commands to download it to the local system.
Sender Outbox –> Source Mail Server –> Interim Mail Server –> Destination Mail Server –> Destination Inbox
This Organized and predictable nature of E-mail means that one could possibly identify the source of an e-mail by simply reverse engineering the path traveled by it. each Time an e-mail is sent on the internet, it not only carries the message body, but also transmits relevant information on the path taken by it. This Information is known as the e-mail Header of the e-mail. Hence, when one receives an abusive e-mail one need not simply delete it helplessly but explore for its source.

1. Are You Being Blackmailed or Threatened through e-mail for large amount of money?
2. Are your employees, partners or alliances receiving foul e-mails that are hampering your day-to-day business activities?
Most modern days Internet Users use standard e-mail clients (Like Outlook Express, Microsoft Outlook, Eudora Pro, Opera Etc.) to send and receive e-mail messages on the Internet. Such e-mail clients are not only very quick and easy to use, but also provide users with a variety of useful features.E-mail clients make it very easy for one to turn a blind eye to the inner working of e-mails systems. However, understanding how e-mail system work is extremely important if one actually wants to be able to solve email related threats.
It is extremely important for Internet Users To Understand How E-mails travel on the Internet. Unless one becomes familiar with the working of e-mail systems, it is impossible to counter such threats.
All Email Communication on the Internet Is Governed by rules and regulations laid by two different Protocols:-
Simple Mail Transfer Protocol (SMTP Port 25)
Post Office Protocol (POP Port 110).
Basically, The e-mail system is quite analogous to that of snail mail. Each time an e-mail has to be sent, the sender connects to a local mail server (Post Office) and uses predefined SMTP Commands to create and send the email. This local mail server then uses the SMTP protocol to route the E-mail through several other interim mail servers, until the e-mail Finally reaches the destination mail server (Post Office). The recipient of the E-mail Then Connects to Destination post office server to download the received e-mail using predefined POP Commands.
The SMTP (Simple Mail Transfer Protocol) is used to send e-mails, while the POP protocol is used to receive them.
To recapitulate, each e-mail on the internet originates at the sender post office server (With the help of SMTP Commands), is routed via a number of interim mail servers and then finally reaches the destination post office where the receiver uses POP commands to download it to the local system.
Sender Outbox –> Source Mail Server –> Interim Mail Server –> Destination Mail Server –> Destination Inbox
This Organized and predictable nature of E-mail means that one could possibly identify the source of an e-mail by simply reverse engineering the path traveled by it. each Time an e-mail is sent on the internet, it not only carries the message body, but also transmits relevant information on the path taken by it. This Information is known as the e-mail Header of the e-mail. Hence, when one receives an abusive e-mail one need not simply delete it helplessly but explore for its source.
if You Have Any Query Regarding This Tutorial Ask In Comments …. Thanks For Visiting…..
Also Bookmark This Blog And Subscribe To Free Email Notification Updates From Below Free Burner
Share With Your Friends If You Want to Say Thanks …..
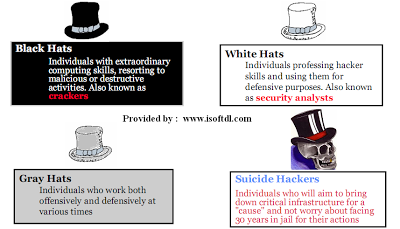
Today I will explain the difference between hacker and cracker. There are lots of articles on internet about the difference between hackers and crackers. In those articles, authors or publishers often try to correct the public misconceptions. For many years, media has erroneously associated the hacker word with a cracker. The general public now believes hacker is someone who breaks into computer systems, hacking passwords and websites and misusing information. This conception is absolutely untrue and demoralizes some of our most talented hackers.
You can see for yourself the scope of the misconception: the world’s most popular authentic source, WIKIPEDIA, has defined hackers in a incorrect way.
There is a very thin line separating hackers and crackers. Just like a coin has two sides, heads and tails, so do computer experts. Some use their techniques and expertise to help the others and secure the systems or networks; some misuse their skills for their own selfish reasons.
There are several traditional ways to determine the difference between hackers and crackers. I will discuss these ways in order of their acceptance in the computer and IT market. First, let’s review the definitions of “hacker” and “cracker.”
These definitions are as follows:
Hackers: A Hacker is a person who is extremely interested in exploring the things and recondite workings of any computer system or networking system. Most often, hackers are expert programmers. These are also called Ethical Hackers or white hat hackers. The technique they use is called ethical hacking.
Hello friends, welcome back today i am going to share with you all possible ways to hack admin or administrator account in windows XP. Today i will explain how to hack admin or administrator account in just 2 minutes. So guys get ready to hack your friends systems in 2 minutes.
Most of times specially in our college we don’t have the access to the admin account, now suppose you want to install a software on that system. What you will do now? Ask the admin to enter the password for you or simply hack it by yourself. I will tell you frankly that i have never opted method one in my life. Whenever i need administrator right i have hacked it but guys don’t do it like that ways because i got suspended from lab twice for doing that.
There are four ways to hack the admin password:
1. Simply accessing Unprotected Administrator Account.
2. Hacking Through Net User Command.
3. Hacking Using the ERD(Emergency Rescue Disk) Commander.
4. Resetting admin password using Ubuntu Live CD or DVD.
Lets start from the first technique to hack the admin or administrator password..
1. Simply Accessing the Unprotected Admin or Administrator account.
How this hack works ? When we install windows XP on our system we usually rename the username as our name or some other keyword. But windows always creates the administrator account whenever we set up windows XP. So when you create your user account during install , windows creates two accounts that is one is your username account and other is Administrator account. But the main thing is that you will only see the account with your username and the Administrator account is hidden but its there and you can easily access that using the following steps:
Step1: Start your computer.
Step2: Now let it start until the windows user’s username appears as shown in snapshot below…
Step3: As This Window Appears Press Ctrl+Alt +Delete (2 times).. Now the Windows like shown below appears..
Step4: Now as shown above Enter the Administrator on the Username box and press enter… Now you will be login in the admin account can easily rest the password…
For Resetting password you can follow two Procedures..
Procedure 1: Goto Start –> Control Panel –> User Accounts.. Now select the account whose password u want to reset.
Procedure 2 : Follow the Next method i.e hacking password through Net User Command.
Note: Hack 1 will only work if Administrator(default) is unsecured i.e User as some other username like above shown figure…
2. Hacking admin or administrator account using net user command
Note: This will work only when user has access of user account or some how he has been allowed or working in admin account.
Steps to hack admin account:
Step1: Goto the Start and click on Run and Type cmd and press enter …
Step 2: Now type “net user” in the command prompt to obtain the All accounts on that computer.. as shown in figure..
Step 3: Now Select the account Which u want to Reset the Password…
Suppose that we want to Reset the Password of Administrator…
Now Type “net user Administrator * “ Without quotes… and press Enter. As shown in the Below Figure..
Step 4: Now after that press Enter Twice to rest the password. Now Next time u open that Account .. It will not require any Password..
3. Hacking admin account using ERD commander (100% working hack)
This hack has no restrictions , using this hack you can hack each and every computer.
First of all Download the ERD(Emergency Rescue Disk) commander… Extract the Files and Make a CD…
DOWNLOAD
STEPS INVOLVED :
1. Insert the ERD Commander Boot CD into the drive and restart the system
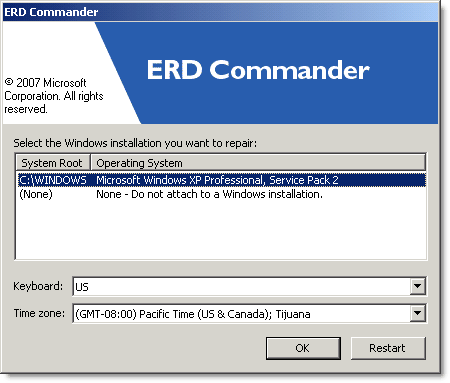
2. Boot the computer using ERD Commander Boot CD. You may have to set the boot order in the BIOS first.
3. Select your Windows XP installation from the list as shown.
2. Boot the computer using ERD Commander Boot CD. You may have to set the boot order in the BIOS first.
3. Select your Windows XP installation from the list as shown.
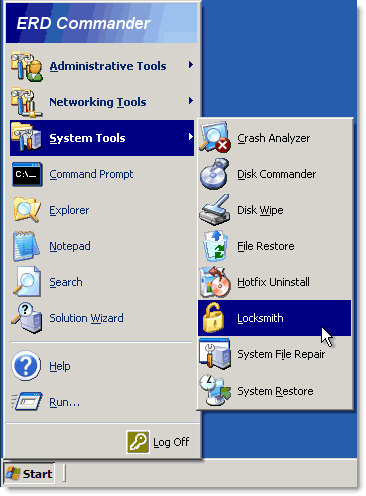
4. From the ERD Commander menu (Start menu), click System Tools and click Locksmith
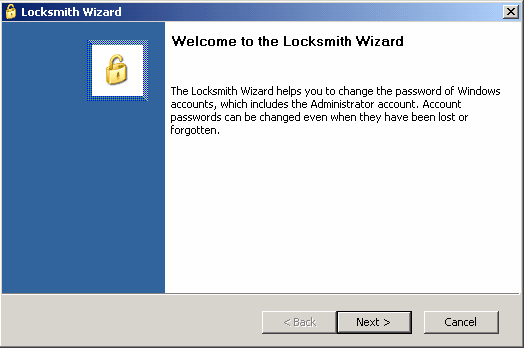
5. Click Next
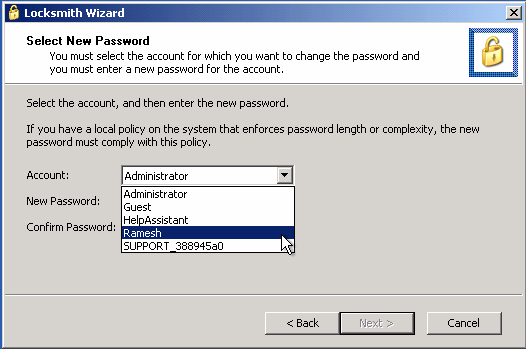
6. Select the administrator account from the list for which you want to reset the password.
7. Type the new password in both the boxes, click Next and click Finish
8 . Restart The System and take the CD out of the Drive..And Enjoy Admin account…
Method 4: Resetting windows password using Ubuntu Live CD or DVD
For this hack you will require the Ubuntu Live CD.
Steps involved :
- Insert Ubuntu Live CD and boot from it.
- Open terminal and install chntpw in Ubuntu. To do so use the following commands.sudo apt-get update
sudo apt-get install chntpw - Now mount your Windows volume. In my case it was dev/sda1. Replace it with yours.sudo mkdir /media/WINDOWS
sudo mount /dev/sda1 /media/WINDOWS - Now navigate to the Windows configuration folder.cd /media/WINDOWS/WINDOWS/system32/config/
- To reset the administrator password entersudo chntpw SAM
- After completing this command you will see 5 different choices. Select the 1st one and press Enter and its done.
- Now restart your system, it will not ask any password.
I hope you all have liked the topics for more such hacks keep visiting our website.
IF YOU HAVE ANY QUERIES ASK ME!
IF YOU HAVE ANY QUERIES ASK ME!









No comments