Hacking Class 10 -How To Prevent Urself from Scanning??
Hacking Class 10 -How To Prevent Urself from Scanning??
Till Now We have Discussed that How to extract the Information about the Site and Individual/site/organisation and scanning them for getting live ports or vulnerabilities to attack them.
Today I will explain you How to Prevent Yourself from Scanning.. and Tomorrow I will give you the Live demonstration of hacking and attacking a website with complete snapshots.
First of all you should know How to protect yourself from these attacks… Its really important that you should know the Counter measures of what you are doing… In case you will face the same problem yourself…:P
THESE ARE THE CERTAIN STEPS AND THINGS YOU SHOULD REMEMBER:
1. Use a Good Firewall to block all the illegal port activity. The Firewall blocks almost all unauthorized attempts by attackers except the following Ports i.e Firewall doesn’t monitor port 80,8080,8181,3128,53.
Now You should Know Which Port Stands for What…
Port 80 is for servers(webservers).
Port 8080 is for HTTP clients.
Port 8181 is for HTTPS clients.
Port 3128 is a active port Needed for all Network processes.
Port 53 is for DNS.
Now If you Have a Good Firewall all illegal activity other than these ports can be blocked. Now the Only chance to being attacked is through 80,8080 and 8181. i.e through websites…When you open some malicious website containing malware scripts there are most chances of being attacked.
So from this you can guess What will be the Second point…Right..
2. Use a Good Web Shield Preferable AVG or any other Good Web shield. This will prevent you from attack through websites…
3. Third way to get attacked is through softwares.
As we all know most of us use Pirated Softwares and Download it from anywhere i.e where we find it and also we doesn’t know the Uploaders…
This is the currently going practice Nowadays. Hackers upload softwares and attach a malicious softwares and hack tools with them like keyloggers, trojans, spywares etc.. with them. Now Here user Himself downloads the attacker files. SO there must be something to prevent from this attack. You can guess for what I am talking…
Ya Surely I am talking about Good Antivirus... I will recommend all to use AVIRA Antivirus and KASPERSKY. Its because of their interativeness.
4. Fourth Point And most Important One…Please Note Most Important One...
Note: It took only 50 sec to 1 minute to scan the system and 3 minutes to attack any system and damage it.
Why I am saying this Important its because no tool is made to detect these type of attacks…If you open this nothing can prevent you from attacked…
So prevention is better than Cure. Don’t open them. For which I am talking.
I am talking about anonymous mails and spams in your Email ID’s. Point to remember 3 out of 1 mail is a spam and 5 out of 1 contains a virus or attack script. Nowadays you will get emails like you have won 100000$ or something like these… these all mails are BOTNETS., these are viruses. they all are asking you about your personal Information and ask you to follow the Link..
You all have noticed that when you click the link it shows Redirecting …around 30 sec ..and then just show you are not eligible for this or this offer is not available in you country… Between the time when they say redirectingggg… they are scanning your system…..and if they find something on you system they attack your system and get access to it…
Sooooooo, DON’T open the mails that come from some anonymous source…
This is all about Scanning Part .. I think you all will like this..
If you have any queries ask me.. I will reply soon.
Today I will explain you How to Prevent Yourself from Scanning.. and Tomorrow I will give you the Live demonstration of hacking and attacking a website with complete snapshots.
First of all you should know How to protect yourself from these attacks… Its really important that you should know the Counter measures of what you are doing… In case you will face the same problem yourself…:P
THESE ARE THE CERTAIN STEPS AND THINGS YOU SHOULD REMEMBER:
1. Use a Good Firewall to block all the illegal port activity. The Firewall blocks almost all unauthorized attempts by attackers except the following Ports i.e Firewall doesn’t monitor port 80,8080,8181,3128,53.
Now You should Know Which Port Stands for What…
Port 80 is for servers(webservers).
Port 8080 is for HTTP clients.
Port 8181 is for HTTPS clients.
Port 3128 is a active port Needed for all Network processes.
Port 53 is for DNS.
Now If you Have a Good Firewall all illegal activity other than these ports can be blocked. Now the Only chance to being attacked is through 80,8080 and 8181. i.e through websites…When you open some malicious website containing malware scripts there are most chances of being attacked.
So from this you can guess What will be the Second point…Right..
2. Use a Good Web Shield Preferable AVG or any other Good Web shield. This will prevent you from attack through websites…
3. Third way to get attacked is through softwares.
As we all know most of us use Pirated Softwares and Download it from anywhere i.e where we find it and also we doesn’t know the Uploaders…
This is the currently going practice Nowadays. Hackers upload softwares and attach a malicious softwares and hack tools with them like keyloggers, trojans, spywares etc.. with them. Now Here user Himself downloads the attacker files. SO there must be something to prevent from this attack. You can guess for what I am talking…
Ya Surely I am talking about Good Antivirus... I will recommend all to use AVIRA Antivirus and KASPERSKY. Its because of their interativeness.
4. Fourth Point And most Important One…Please Note Most Important One...
Note: It took only 50 sec to 1 minute to scan the system and 3 minutes to attack any system and damage it.
Why I am saying this Important its because no tool is made to detect these type of attacks…If you open this nothing can prevent you from attacked…
So prevention is better than Cure. Don’t open them. For which I am talking.
I am talking about anonymous mails and spams in your Email ID’s. Point to remember 3 out of 1 mail is a spam and 5 out of 1 contains a virus or attack script. Nowadays you will get emails like you have won 100000$ or something like these… these all mails are BOTNETS., these are viruses. they all are asking you about your personal Information and ask you to follow the Link..
You all have noticed that when you click the link it shows Redirecting …around 30 sec ..and then just show you are not eligible for this or this offer is not available in you country… Between the time when they say redirectingggg… they are scanning your system…..and if they find something on you system they attack your system and get access to it…
Sooooooo, DON’T open the mails that come from some anonymous source…
This is all about Scanning Part .. I think you all will like this..
If you have any queries ask me.. I will reply soon.
As we have covered almost all topics of scanning this is the last topic that come under scanning….
First of all ..
WHAT IS IP SPOOFING??
Ip spoofing is basically encrypting your Ip address so that it appears something else to attacker or victim i.e it is the virtual Ip address..
~ IP Spoofing is when an attacker changes his IP address so that he appears to be someone else.
~ When the victim replies back to the address, it goes back to the spoofed address and not to the attacker’s real address.
~ You will not be able to complete the three-way handshake and open a successful TCP connection by spoofing an IP address.
You Will Better Understand It With SNAPSHOT..
HOW TO DETECT IP SPOOFING ??
When an attacker is spoofing packets, he is usually at a different location than the address being spoofed
Attacker’s TTL(Time to Live i.e Time for which IP is allocated for use) will be different from the spoofed address’ real TTL. If you check the received packet’s TTL with spoofed one, you will see TTL doesn’t match.
These things are blocked in latest versions of Windows i.e after SP3. Firewall will itself block any spoofing attacks…
This Is all about the IP spoofing and Scanning Part.
The Next Two Parts of upcoming class:
1. How to Protect Yourself From Scanning .
2. How to Hack Websites Using things that We Studied until Now . A little SQL injection tutorial is also required for that. We will try to cover it as quick as Possible..
If you have any doubts about Ip spoofing you can ask..
Continuing from the Previous Lecture on Removing and Hiding Our Traces . Today we will discuss the Remaining four Points that we discussed tomorrow… So read on..
Tool to Bypass Government Censor : Psiphon Tool
DOWNLOAD:
http://www.eccouncil.org/cehtools/psiphon.zip
For More Details About Tool Visit:
http://psiphon.ca/
How To Bypass Google Tracing and What’s the Need??
First I will tell you the Need . Everything that We searches over the Net i.e through google , Google makes a log of us … Log contains 4 basic fields :
1. IP address
2. Search Query
3. ISP from which search is made
4. Time ,date,year etc..
Did you know that Google stores a unique identifier in a cookie on your PC, which allows them to track the keywords you search for? They use this information to compile reports, track user habits, and test features. In the future, it is possible they could even sell this information or share it with others. Even worse, Google’s cookie isn’t set to expire until the year 2038, unless you delete it first.
Now If you do anything that doesn’t pass google censorship then you will surely going to suffer.
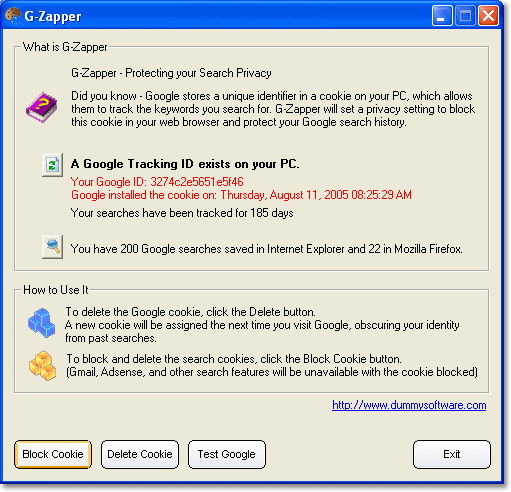
TOOL TO BYPASS GOOGLE TRACING : G-Zapper
G-Zapper helps protect your identity and search history. G-Zapper will read the Google cookie installed on your PC, display the date it was installed, determine how long your searches have been tracked, and display your Google searches. G-Zapper allows you to automatically delete or entirely block the Google search cookie from future installation.
SNAPSHOT:
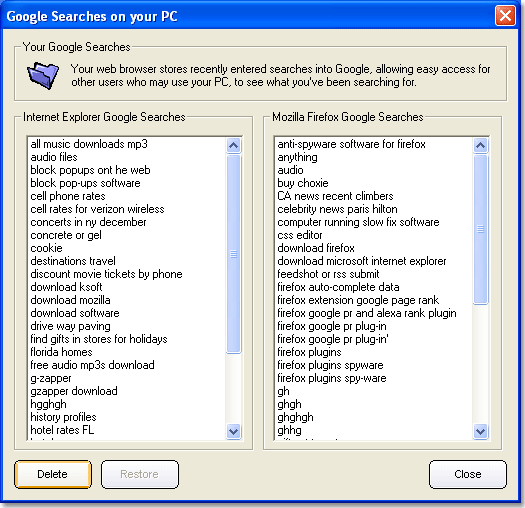
SAMPLE LOOK UP OF YOUR SEARCHES:
DOWNLOAD:
http://www.dummysoftware.com/gzapper.html
Sorry Guys Currently my version of this software has expired so you have to work with trial..
We Will Continue Discussion in evening…
If you have any Queries Ask me..
Tool to Bypass Government Censor : Psiphon Tool
- Psiphonis a censorship circumvention solution that allows users to access blocked sites in countries where the Internet is censored.
- Psiphonturns a regular home computer into a personal, encrypted server capable of retrieving and displaying web pages anywhere .
- Psiphonacts as a “web proxy” for authenticated psiphonites, retrieving requested web pages and displaying them in a user’s browser.
- Psiphonuses a secure, encrypted connection to receive web requests from the psiphoniteto the psiphonode who then transports the results back to the psiphonite.
DOWNLOAD:
http://www.eccouncil.org/cehtools/psiphon.zip
For More Details About Tool Visit:
http://psiphon.ca/
How To Bypass Google Tracing and What’s the Need??
First I will tell you the Need . Everything that We searches over the Net i.e through google , Google makes a log of us … Log contains 4 basic fields :
1. IP address
2. Search Query
3. ISP from which search is made
4. Time ,date,year etc..
Did you know that Google stores a unique identifier in a cookie on your PC, which allows them to track the keywords you search for? They use this information to compile reports, track user habits, and test features. In the future, it is possible they could even sell this information or share it with others. Even worse, Google’s cookie isn’t set to expire until the year 2038, unless you delete it first.
Now If you do anything that doesn’t pass google censorship then you will surely going to suffer.
TOOL TO BYPASS GOOGLE TRACING : G-Zapper
G-Zapper helps protect your identity and search history. G-Zapper will read the Google cookie installed on your PC, display the date it was installed, determine how long your searches have been tracked, and display your Google searches. G-Zapper allows you to automatically delete or entirely block the Google search cookie from future installation.
SNAPSHOT:

SAMPLE LOOK UP OF YOUR SEARCHES:

DOWNLOAD:
http://www.dummysoftware.com/gzapper.html
Sorry Guys Currently my version of this software has expired so you have to work with trial..
We Will Continue Discussion in evening…
If you have any Queries Ask me..
NOTE : STRICTLY FOR EDUCATIONAL PURPOSES.. I AND Hackingloops IS NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITY AND MISUSE…
Hey guys as I have Already Mentioned above this is only for educational purpose so don’t misuse it. I and Isoftdl is not responsible for any malpractice… Now you all thinking why I am saying this.. Itz pity simple because Its the most dangerous part i.e Hiding your identity from being traced by anyone i.e government,ISP,Raw…everything… So Read On…
Let’s have a Breif Look up of Topics That we Cover Here:
1. Proxies and Anonymous Web Browsers
2. Anonymizers
3. Tools to bypass Government Censorship :P
4. Tools to Bypass Google Tracing :P
5. HTTP Tunneling for Windows
6. IP spoofing :P
Today we Will Cover First two Topics…
FIRST OF ALL ..
WHAT IS PROXY AND HOW IT WORKS???
Proxy is a network computer that can serve as an intermediate for connection with other computers .
They are usually used for the following purposes:
• As a firewall, a proxy protects thelocal network from outside access.
• As an IP addresses multiplexer, a proxy allows the connection of a number of computers to the Internet
when having only one IP address.
• Proxy servers can be used (to some extent) to anonymize web surfing.
• Specialized proxy servers can filter out unwanted content, such as ads or ‘unsuitable’ material.
• Proxy servers can afford some protection against hacking attacks. (For Our Purpose)
HOW AND WHY TO GET FREE PROXY SERVERS ??
~ Attacks using thousands of proxy servers around the world are difficult to trace.
~ Thousands of free proxy servers are available on the Internet .
~ Search for “free proxy servers” in Google .
~ Using proxy servers can mask your trace .
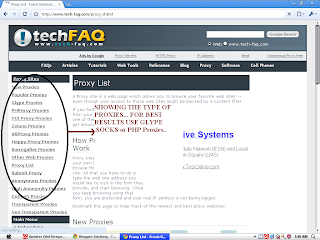
I will recommend two sites for getting the Free Proxy servers. As these sites Daily provides Fresh anonymous Proxies…
1. http://www.tech-faq.com/proxy.shtml (provides almost all type of Proxies)
2. http://proxy.org/ (check the Right Hand Side For Proxies)
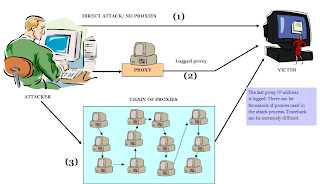
BELOW SNAP SHOWING HOW PROXIES USED TO ATTACK..
ANONYMOUS WEB BROWSERS
Anonymous Web Browsers have inbuilt proxy finders they search for proxies by default and make our surfing anonymous…
TWO BEST ANONYMOUS WEB BROWSERS ARE:
1. Invisible Browsing v7.0
SNAPSHOT:

2. BrowZar 2.0
DOWNLOAD:
http://www.browzar.com/download/index.html
SNAPSHOT:
You can also find more by googling it but these two are just Best.. :P
ANONYMIZERS
Anonymizers are services that help to make web surfing anonymous. The first anonymizer developed was Anonymizer.com, created in 1997 by Lance Cottrel.
An anonymizer removes all the identifying information from a user’s computers while the user surfs the Internet, thereby ensuring the privacy of the user.
Why Use Anonymizer?
• Example: Google.com keeps track of all your web searches on their servers by placing a cookie on your machine.
• Every single search you entered at Google is logged.
SEVERAL ANONYMIZER TOOLS ARE:
1. Hide Platinum IP
2. Hide My IP
3.Hide My Ip Address
Note: I am not providing the Below Three Because Almost 99% of their cracked version contains viruses and Spywares which can cause damage to your system…
The Rest Four Topics About Hiding Our Traces We will discuss Tomorrow..
Hope that You all have Like This…
IF you have Any Queries ASK in FORM OF COMMENTS !










No comments