Hacking Class 6 – Vulnerability Scanning And Tools
Hacking Class 6 – Vulnerability Scanning And Tools
In my previous class I have discussed about OS fingerprinting i.e finding that which OS the Victim is using.
Now We move further in scanning phase and now we will scan the systems for vulnerabilities i.e finding the weakness in security ,OS,database and so on..
What is Vulnerability???
As I have Told in First class that Vulnerability is weakness in the network,system,database etc… We can call vulnerability as the Loophole i.e through which victim can be attacked.. We first analyze the loophole and then try to use it to best to Hack the System of victim or oraganisation or website…
TOOL THAT WE USE FOR VULNERABILITY SCANNING ARE :
1. Nessus
2. Retina
NESSUS
The Nessus® vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks.
Features:
~ Plug-in-architecture
~ NASL (Nessus Attack Scripting Language)
~ Can test unlimited number of hosts simultaneously
~ Smart service recognition
~ Client-server architecture
~ Smart plug-ins
~ Up-to-date security vulnerability database
SAMPLE SNAPSHOT:
DOWNLOAD NESSUS :
http://www.nessus.org/download/
RETINA
Retina Network Security Scanner, the industry and government standard for multi-platform vulnerability management, identifies known and zero day vulnerabilities plus provides security risk assessment, enabling security best practices, policy enforcement, and regulatory audits.
Features:
~ Retina network security scanner is a network vulnerability assessment scanner.
~ It can scan every machine on the target network, including a variety of operating system platforms, networking devices, databases, and third party or custom applications.
~ It has the most comprehensive and up-to-date vulnerability database and scanning technology.
SAMPLE SNAPSHOT:
DOWNLOAD RETINA:
http://www.eeye.com/html/products/retina/download/index.html
Now After Scanning the Systems for Vulnerabilites .. We will Now Going to attack the Systems but before this we should know the Risk . This risk can be reduced to great extent by using Proxies.. In Next Class We will Discuss what are Proxies and How they work and how they are going to Help us and some undetectable and untraceable Proxy servers…
So wait For Next Class…. And Keep Learning…
If you Have Any Queries You can Ask In form Of Comments!
Now We move further in scanning phase and now we will scan the systems for vulnerabilities i.e finding the weakness in security ,OS,database and so on..
What is Vulnerability???
As I have Told in First class that Vulnerability is weakness in the network,system,database etc… We can call vulnerability as the Loophole i.e through which victim can be attacked.. We first analyze the loophole and then try to use it to best to Hack the System of victim or oraganisation or website…
TOOL THAT WE USE FOR VULNERABILITY SCANNING ARE :
1. Nessus
2. Retina
NESSUS
The Nessus® vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks.
Features:
~ Plug-in-architecture
~ NASL (Nessus Attack Scripting Language)
~ Can test unlimited number of hosts simultaneously
~ Smart service recognition
~ Client-server architecture
~ Smart plug-ins
~ Up-to-date security vulnerability database
SAMPLE SNAPSHOT:
DOWNLOAD NESSUS :
http://www.nessus.org/download/
RETINA
Retina Network Security Scanner, the industry and government standard for multi-platform vulnerability management, identifies known and zero day vulnerabilities plus provides security risk assessment, enabling security best practices, policy enforcement, and regulatory audits.
Features:
~ Retina network security scanner is a network vulnerability assessment scanner.
~ It can scan every machine on the target network, including a variety of operating system platforms, networking devices, databases, and third party or custom applications.
~ It has the most comprehensive and up-to-date vulnerability database and scanning technology.
SAMPLE SNAPSHOT:
DOWNLOAD RETINA:
http://www.eeye.com/html/products/retina/download/index.html
Now After Scanning the Systems for Vulnerabilites .. We will Now Going to attack the Systems but before this we should know the Risk . This risk can be reduced to great extent by using Proxies.. In Next Class We will Discuss what are Proxies and How they work and how they are going to Help us and some undetectable and untraceable Proxy servers…
So wait For Next Class…. And Keep Learning…
If you Have Any Queries You can Ask In form Of Comments!
In the Previous class I have discussed the very basic things about scanning and two most important scanning tools namely NMAP and Nettools. Now we continue our discussion on the Scanning …
Now we Discuss some internal and advanced scanning Methods..
First of Which is OS Fingerprinting…
What is OS Fingerprinting ??
OS fingerprinting is the method to determine the operating system that is running on the target system.
The two different types of fingerprinting are:
• Active stack fingerprinting
• Passive fingerprinting
Active Stack FingerPrinting:
Based on the fact that OS vendors implement the TCP stack differently.Specially crafted packets are sent to remote OSs and response is noted. The responses are then compared with a database to determine the OS.
Passive FingerPrinting:
Passive banner grabbing refers to indirectly scanning a system to reveal its server’s operating system.
It is also based on the differential implantation of the stack and the various ways an OS responds to it.
It uses sniffing techniques instead of the scanning techniques. It is less accurate than active fingerprinting.
TOOL USED FOR OS FINGERPRINTING :p0f Os Fingerprinting Tool
DOWNLOAD:
http://lcamtuf.coredump.cx/p0f-win32.zip
Now we Discuss some internal and advanced scanning Methods..
First of Which is OS Fingerprinting…
What is OS Fingerprinting ??
OS fingerprinting is the method to determine the operating system that is running on the target system.
The two different types of fingerprinting are:
• Active stack fingerprinting
• Passive fingerprinting
Active Stack FingerPrinting:
Based on the fact that OS vendors implement the TCP stack differently.Specially crafted packets are sent to remote OSs and response is noted. The responses are then compared with a database to determine the OS.
Passive FingerPrinting:
Passive banner grabbing refers to indirectly scanning a system to reveal its server’s operating system.
It is also based on the differential implantation of the stack and the various ways an OS responds to it.
It uses sniffing techniques instead of the scanning techniques. It is less accurate than active fingerprinting.
TOOL USED FOR OS FINGERPRINTING :p0f Os Fingerprinting Tool
DOWNLOAD:
http://lcamtuf.coredump.cx/p0f-win32.zip
P0f v2 is a versatile passive OS fingerprinting tool. P0f can identify the operating system on:
- machines that connect to your box (SYN mode),
- machines you connect to (SYN+ACK mode),
- machine you cannot connect to (RST+ mode),
- machines whose communications you can observe.
P0f can also do many other tricks, and can detect or measure the following:
- firewall presence, NAT use (useful for policy enforcement),
- existence of a load balancer setup,
- the distance to the remote system and its uptime,
- other guy’s network hookup (DSL, OC3, avian carriers) and his ISP.
We will continue class on scanning in the evening…Today I will explain more about scanning.. So wait for Next article…
If You Have Any Queries ask Me … I will Help You
Out !
In my Previous class I have explained about footprinting i.e getting the IP of the Person/website/organisation whom you want to attack and extracting the personal Information.. You all were thinking that what was the use of that .. In this class you will came to know why we have undergo footprinting and analysis part…
In Scanning Part We Will Cover the Following Topics in details :
~ Definition of scanning
~ Types and objectives of Scanning
~ Understanding Scanning methodology
~ Checking live systems and open ports
~ Understanding scanning techniques
~ Different tools present to perform Scanning
~ Understanding banner grabbing and OS fingerprinting
~ Drawing network diagrams of vulnerable hosts
~ Preparing proxies
~ Understanding anonymizers
~ Scanning countermeasures
What Is Scanning ?? And Why We Focus On that ?
Scanning as from the name means that we will scan something to find some details etc etc… Scanning basically refers to the gathering of following four informations…
We Scan systems for four basic purposes :-
The various types of scanning are as follows:
~Port Scanning
~Network Scanning
~Vulnerability Scanning
I want to Define These Terms here Only as they are of great use in further tutorial…
PORT SCANNING : There are 64k ports in a computer out of which 1k are fixed for system or OS services. In Port scanning we scan for the open Ports which can be used to attack the victim computer.
In Port scanning a series of messages sent to break into a computer to learn about the computer’s network services. Through this we will know that which port we will use to attack the victim..
Network Scanning : Network scanning is basically a procedure of finding the active hosts on the Network.
i.e We tries to find that system is standalone or multiuser…
This is done either for the purpose of attacking them or for network security assessment i.e how secured the network Is ??
Vulnerability Scanning : As from the name , In this type of scanning We scan the systems for finding the vulnerability i.e the weakness in OS/database … Once we find the vulnerability or loop hole we can utilize it to Best..and attack the victim through that …
OBJECTIVES OF SCANNING
These are Primary objectives of scanning i.e why do we do scanning :
~ To detect the live systems running on the network.
~ To discover which ports are active/running.
~ To discover the operating system running on the target system (fingerprinting).
~ To discover the services running on the target system.
~ To discover the IP address of the target system.
We will prefer TOOLS for this because they will reduce our Hectic Work… The first Tool that we Use is the NMAP :
DOWNLOAD :http://nmap.org/dist/nmap-5.00-setup.exe
Features of NMAP :
~ Nmap is used to carry out port scanning, OS detection, version detection, ping sweep, and many other techniques.
~ It scans a large number of machines at one time.
~ It is supported by many operating systems.
~ It can carry out all types of port scanning techniques.
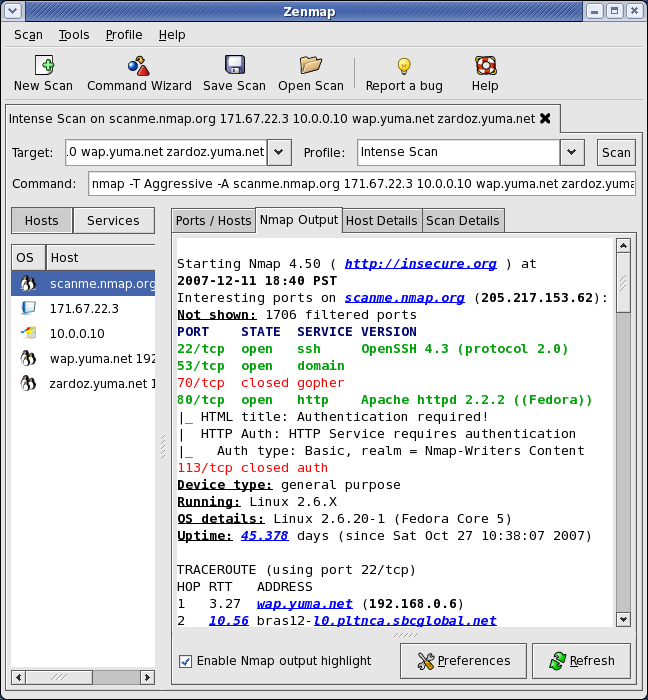
SECOND TOOL IS NET TOOLS 5.0.70 :
Itz is a collection of various Networking Tools … must for beginners…
DOWNLOAD: http://www.softpedia.com/progDownload/Net-Tools-Download-22193.html
~ Net Tools Suite Pack is a collection of scanning tools.
~ This toolset contains tons of port scanners, flooders, web rippers, and mass e-mailers.
Note: Some of these tools may not Work but some are too good.
I thisnk that’s Enough for Today .We will discuss more on scanning tomorrow Until You try these tools..
If you have any problem in Using these tools then you can ask me ..I will help you use these tools…
ENJOY AND HAVE FUN ! IF YOU HAVE ANY QUERIES ASK ME IN FORM OF COMMENTS !
In Scanning Part We Will Cover the Following Topics in details :
~ Definition of scanning
~ Types and objectives of Scanning
~ Understanding Scanning methodology
~ Checking live systems and open ports
~ Understanding scanning techniques
~ Different tools present to perform Scanning
~ Understanding banner grabbing and OS fingerprinting
~ Drawing network diagrams of vulnerable hosts
~ Preparing proxies
~ Understanding anonymizers
~ Scanning countermeasures
What Is Scanning ?? And Why We Focus On that ?
Scanning as from the name means that we will scan something to find some details etc etc… Scanning basically refers to the gathering of following four informations…
We Scan systems for four basic purposes :-
- To find specific IP address
- Operating system
- System Architecture
- Services Running on system
The various types of scanning are as follows:
~Port Scanning
~Network Scanning
~Vulnerability Scanning
I want to Define These Terms here Only as they are of great use in further tutorial…
PORT SCANNING : There are 64k ports in a computer out of which 1k are fixed for system or OS services. In Port scanning we scan for the open Ports which can be used to attack the victim computer.
In Port scanning a series of messages sent to break into a computer to learn about the computer’s network services. Through this we will know that which port we will use to attack the victim..
Network Scanning : Network scanning is basically a procedure of finding the active hosts on the Network.
i.e We tries to find that system is standalone or multiuser…
This is done either for the purpose of attacking them or for network security assessment i.e how secured the network Is ??
Vulnerability Scanning : As from the name , In this type of scanning We scan the systems for finding the vulnerability i.e the weakness in OS/database … Once we find the vulnerability or loop hole we can utilize it to Best..and attack the victim through that …
OBJECTIVES OF SCANNING
These are Primary objectives of scanning i.e why do we do scanning :
~ To detect the live systems running on the network.
~ To discover which ports are active/running.
~ To discover the operating system running on the target system (fingerprinting).
~ To discover the services running on the target system.
~ To discover the IP address of the target system.
We will prefer TOOLS for this because they will reduce our Hectic Work… The first Tool that we Use is the NMAP :
DOWNLOAD :http://nmap.org/dist/nmap-5.00-setup.exe
Features of NMAP :
~ Nmap is used to carry out port scanning, OS detection, version detection, ping sweep, and many other techniques.
~ It scans a large number of machines at one time.
~ It is supported by many operating systems.
~ It can carry out all types of port scanning techniques.

SECOND TOOL IS NET TOOLS 5.0.70 :
Itz is a collection of various Networking Tools … must for beginners…
DOWNLOAD: http://www.softpedia.com/progDownload/Net-Tools-Download-22193.html
~ Net Tools Suite Pack is a collection of scanning tools.
~ This toolset contains tons of port scanners, flooders, web rippers, and mass e-mailers.
Note: Some of these tools may not Work but some are too good.
I thisnk that’s Enough for Today .We will discuss more on scanning tomorrow Until You try these tools..
If you have any problem in Using these tools then you can ask me ..I will help you use these tools…
ENJOY AND HAVE FUN ! IF YOU HAVE ANY QUERIES ASK ME IN FORM OF COMMENTS !
Yesterday I have explained You all that How to collect information about the Websites and organisations….
Today i will continue With Footprinting and take you to some more deep level… And then tell you how to make Blueprints from them.. So read on….
UNEARTHING BASIC INFORMATION
First of all We will focus on Unearthing the Basic Information about the site… i.e the IP and server informations..
I will Show you with the help on snapshots :
First go to START –> RUN —>type cmd—>then type tracert www.websitename.com
Here we will use two basic commands in command Prompt(cmd): tracert www.webistetobeanlysed.com
and ping www.websitename.com
It will look something like this:
Here I explain what it shows…
We trace routed www.amulive.com
1. Shows Our Gateway of connectivity.
2. Shows our Outgoing Footprint Ip(i.e the our IP that is being analyzed by website)
3. Shows Connectivity passes through which service Provider. I uses BSNL but its showing airtel because I prefer DNS of Airtel for surfing Quick).
Next steps showing the Ip’s of Webservers through which amulive is being maintained.
After This We will came to now the IP of the Website and Ip of itz web servers which are being used further.
website Ip can be used to gather more information about the website..
How to Find The Personal Information About the Individual Over Net ??
Its one of the Most important task. Its also helpful in finding the fake profiles… But unfortuantely this is limited But we can use it to the Most… There are two website which will help us…
1. http://people.yahoo.com ( best Site To trace People for their Personal Information and also reverse Phone or mobile number Look up)
2. http://www.intellius.com ( But this site is limited to US only)
Sample Report from Intellius :
Now Using these Sites you will be able to collect the personal information of the individuals and also being able to identify the fake profiles..
TOOLS NEEDED FOR FOOTPRINTING :
You can avoid above hectic work by using this tool : SpiderFoot
Download link: http://www.binarypool.com/spiderfoot/
Information about SpiderFoot:
ADDITIONAL FOOTPRINTING TOOLS :
Note all these tools are freewares .. U can easily google then and download these..
~ Whois
~ Nslookup
~ ARIN
~ Neo Trace
~ VisualRoute Trace
~ SmartWhois
~ eMailTrackerPro
~ Website watcher
~ Google Earth
~ GEO Spider
~ HTTrack Web Copier
~ E-mail Spider
This is all about Footprinting . Now Use the Gathered information to make basic Detailed Information about the Website/person…
I thinks This is Enough for Today. Please Comment . If you have any queries Post them in form of comments.
Today i will continue With Footprinting and take you to some more deep level… And then tell you how to make Blueprints from them.. So read on….
UNEARTHING BASIC INFORMATION
First of all We will focus on Unearthing the Basic Information about the site… i.e the IP and server informations..
I will Show you with the help on snapshots :
First go to START –> RUN —>type cmd—>then type tracert www.websitename.com
Here we will use two basic commands in command Prompt(cmd): tracert www.webistetobeanlysed.com
and ping www.websitename.com
It will look something like this:
Here I explain what it shows…
We trace routed www.amulive.com
1. Shows Our Gateway of connectivity.
2. Shows our Outgoing Footprint Ip(i.e the our IP that is being analyzed by website)
3. Shows Connectivity passes through which service Provider. I uses BSNL but its showing airtel because I prefer DNS of Airtel for surfing Quick).
Next steps showing the Ip’s of Webservers through which amulive is being maintained.
After This We will came to now the IP of the Website and Ip of itz web servers which are being used further.
website Ip can be used to gather more information about the website..
How to Find The Personal Information About the Individual Over Net ??
Its one of the Most important task. Its also helpful in finding the fake profiles… But unfortuantely this is limited But we can use it to the Most… There are two website which will help us…
1. http://people.yahoo.com ( best Site To trace People for their Personal Information and also reverse Phone or mobile number Look up)
2. http://www.intellius.com ( But this site is limited to US only)
Sample Report from Intellius :
Satellite Picture of Joe’s House from Intellius:
Now Using these Sites you will be able to collect the personal information of the individuals and also being able to identify the fake profiles..
TOOLS NEEDED FOR FOOTPRINTING :
You can avoid above hectic work by using this tool : SpiderFoot
Download link: http://www.binarypool.com/spiderfoot/
Information about SpiderFoot:
SpiderFoot is a free, open-source, domain footprinting tool. Given one or multiple domain names (and when I say domains, I’m referring to the DNS kind, not Windows domains), it will scrape the websites on that domain, as well as search Google, Netcraft, Whois and DNS to build up information like:
- Subdomains
- Affiliates
- Web server versions
- Users (i.e. /~user)
- Similar domains
- Email addresses
- Netblocks
ADDITIONAL FOOTPRINTING TOOLS :
Note all these tools are freewares .. U can easily google then and download these..
~ Whois
~ Nslookup
~ ARIN
~ Neo Trace
~ VisualRoute Trace
~ SmartWhois
~ eMailTrackerPro
~ Website watcher
~ Google Earth
~ GEO Spider
~ HTTrack Web Copier
~ E-mail Spider
This is all about Footprinting . Now Use the Gathered information to make basic Detailed Information about the Website/person…
I thinks This is Enough for Today. Please Comment . If you have any queries Post them in form of comments.
















No comments