How to find or get IP address of Victim
How to find or get IP address of Victim
Hello friends, today I will explain how to remotely get the IP address of any computer. Using some very basic tricks, we can find the IP address of any remote computer and then you can start hacking into the remote system for things like port scanning and finding vulnerabilities. There are several methods for getting the IP address of a victim, but I will share a few and highlight the best ones that can tell you an IP address in just few clicks. All of these methods are free, manual methods, meaning you do not require any tools.
 |
| How to find or get IP address of somebody else remotely |
4 ways to get the IP address of the Victim or another Computer:
1. Using PHP notification Script
2. Using Blogs and Websites
3. Using Read Notify service
4. Sniffing during Gmail and Yahoo chat sessions
We are here to learn concepts so first I will explain what exactly an IP address is and explain its significance. So friends, a very basic question: what is an IP address? Why is it important for hackers and security professionals?
What is an IP address?
Basically an IP address (Internet Protocol address) is a unique numerical value that is assigned to any computer or printer on a computer network that uses an internet protocol for communication purpose. “Protocol” basically means the rules for communication.
An IP address serves for two basic purposes:
1. Host or network interface identification
2. Location Addressing
For exploring more about IP addressing, check out Wikipedia.
How to Find IP address of another computer?
1. Using PHP notification Script
Using this notification script you can get the IP address in just seconds. Steps of using this PHP script:
a. Download the PHP notify script and extract files.
Download here
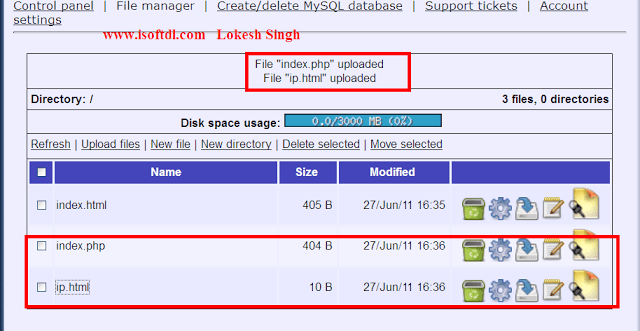
b. Now you will get two files IP.html and index.php . You need to upload these two files to any free web hosting server.
Example: I used www.my3gb.com to upload these two files. Create an account there and upload these two files as shown below.
 |
| Upload Files to free web hosting server |
c. Now you will need to send the link of index.php to the victim whose password you want to get. To get the link, click on index.php as shown in the above snapshot. Now a new window will open copy the link in the address bar and send to the victim.
d. When the victim opens the above link nothing will happen, but his IP address will be written into the ip.html file. Open the ip.html file to get his IP address.
2. Using Blogs and Websites
This method is for those who have their own blogs or websites. Normal users can also do this as blogs are free to make. Create a new blog and choose any stats service, such as histats. Aadd a new widget and put a histats code there and save the template. Send the link of your blog to your victim to get his IP.
3. Using Read Notify service
This is an email based service. Steps to use Read Notify service:
a. First open the Read Notify website: RCPT
b. Register on this website and it will send you a confirmation mail. Verify your account.
c. Once your account is activated take the following steps to use this service:
- Compose an email just like you normally would in your own email or web email program
- Type: .readnotify.com on the end of your recipient’s email address (don’t worry, that gets removed before your recipient receives the email). Like this: shiviskingg@gmail.com.readnotify.
com - Send your email
Some things to remember:
- don’t send to and from the same computer
- if your email program ‘auto-completes’ email addresses from your address book, you’ll need to keep typing over top of the auto-completed one to add the .readnotify.com
- if you are cc-ing your email to other readers, you must add tracking to all of them
4. Sniffing Yahoo and Gmail Chat sessions
With the help of Sniffers like ethereal, wireshark, etc. we can sniff Gmail and Yahoo chat sessions while chatting to our victim and extract the IP address from there. I will explain this trick in detail in my next article as this process is a bit long.
5. Bonus Method for Online Gamers
We can also get IP addresses from online games like Counter Strike and Age of Empires. Many Counter Strike servers use amx mode. View which people are connecting to the servers and plugins will show the IP address of people connecting to the game server. If you have more access to the Counter Strike server you can use status command in console. Go to console, type “status” (without quotes), and press enter. There you can see all players’ details, including steam IDs.
Now you have the IP address, but what can you do with it? Everything, as I will explain in my next article
Now you have the IP address, but what can you do with it? Everything, as I will explain in my next article
I hope you all liked this article. If you have any queries or concerns just ask me in the comments. Thanks for reading.
CME online hacking classes are going to start on Sunday 11, as promised. I have already provided the timings in my previous post “CME hacking class by Hacking loops”. I have said to all of you that i will provide you the presentation prior to hacking class so that you will be able to understand what we gonna discuss in our first hacking class. So friends please find the presentation for the first hacking class and please read it atleast once, so that you will have a idea about what we are going to discuss in that.
Check timings here: CME Timings
 |
| Download Presentation for First Hacking class of CME Hackers |
Topics Covered in First Hacking class:
1. What is Hacking
2. Who are Hackers
3. Different types of hackers and which path we will choose
4. Basic hacking terms
5. How to launch a hacking attempt(regular or irregular)
6. Introduction to Reconnaissance
7. Introduction to scanning and port mapping
8. Basic of Gaining access to victims system
9. Basics of clearing and removing our traces from victims system.
10. Question and Answer session
How you will join CME online hacking class?
We are using combination of two things for our hacking class:
1. Mikogo 4 : For sharing my desktop with all users simultaneously. ( mainly for showing practical examples)
2. Voxli ( For group voice chat)
Note: There is no need to register on both of sites, i will provide you the access codes just before half an hour before, so that you all can join hacking class. You will be able to get those on right sidebar of my websites hackingloops and isoftdl.
DOWNLOAD PRESENTATION
Hope you all liked it. If you have any queries ask me in form of comments. You can also ask your questions during Q n A session in hacking class.
Thanks for reading……
Jai Shri Krishna friends, Today we are starting recruitment to our new Hacking Group CHECKMATE ELITE HACKERS CLUB has been started. I have taken a month to decide how can i reach you in best way and spread cyber security and awareness among my friends and internet user, i have asked a lot of my friends about suggestions and at last i finalizes CHECKMATE. Its not like other Hacking Groups, its special. Go on reading details and what benefits you will get as CHECKMATES.
Are you Beginner in Hacking? Want to Elite Hacker? Want to be an Elite Cyber security and Ethical hacking specialist? Want to choose your career in Ethical Hacking and Cyber Security? Want to hack Hackers? Are you already an Expert or Elite? Be With us, share your knowledge with us and share knowledge to remain as Elite. So if this is your question then Welcome to CHECKMATE ELITE HACKERS CLUB.
Its our PRE-LAUNCH recruitment. First Live Online Hacking class is scheduled on 2 September.
 |
| CHECKMATE ELITE HACKERS CLUB ANNOUNCEMENT |
BENEFITS OF BEING A CHECKMATER:
- Live Free Online Hacking classes with video conferencing by Lokesh Singh. (security auditor of Isoftdl Solutions, CEH and CFSI certified year 2006, Application developer in TCS).
- Live support with Team-viewer daily.
- Presentations and Documents will be shared prior to start of Each Hacking class with users so that they can understand things better.
- Live Practical hacking examples and test environment for users.
- If you have missed any hacking class then don’t worry we will also make video and share it on youtube for you for future reference.
- Most important everything is absolutely free.
SO WHY ARE YOU WAITING FILL THE FORM AND SECURE YOUR POSITION. TOP CONTRIBUTORS WILL ALSO HAVE CHANCE TO BECOME MODERATOR AND BECOMING PART TOP 11 ELITES.
The MAC address uniquely identifies the network card within the current network segment. It consists of a vendor id that is unique among all network vendors, and a relative id that is unique to the vendor. The address is hard-coded onto the network adapter. But since most of the drivers were developed with the Windows Driver Development kit, the MAC address is read from the Windows registry, when the card is initialized. Now when you are launching any hacking attempt your MAC address is registered at your ISP that your physical address has accessed the particular website and you can be easily identified as MAC address is always unique. So be expert Hacker, first remove all things that can be traced back and its the first step..
Steps to change MacAddress of PC1. Note down the description and current MAC address of the card you want to modify.
To do this, open a command prompt and type the following:
Steps to change MacAddress of PC1. Note down the description and current MAC address of the card you want to modify.
To do this, open a command prompt and type the following:
ipconfig /all
as shown below:
 |
| Real Mac address View |
2. The description of the card is in the field “Description“, whereas the MAC address can be found at the field “Physical address“.
3. Start the registry editor by using regedit command in run(regedit under Windows XP, Windows 7, Windows Vista and Windows 2003 server) and open the node
HKEY_LOCAL_MASHINESystemCurrentControlSetControlClass
{4D36E972-E325-11CE-BFC1-08002BE10318}
Click on each of them until you get Network adapter in description as shown below:
 |
| Network Adapter main node |
4. Find the node which contains the field Driver Description in the right pane that matches the description of the network adapter you want to change.
5. Now find the registry key “NetworkAddress” (without quotes). If not found create the new one and choose type String key as shown below:
 |
| Registry View for creating new key |
6. Double click the entry “NetworkAddress” and enter the new network address. Note that the new network address should have exactly twelve digits as shown below:
 |
| Entering value of Network address key. |
7. Once you entered the new network address, the network adapter has to be restarted. To do this, open the control panel and then “Network and Dialup connections”. Right click the network connection you have just modified, and then click disable. After the device has been disabled, right-click the connection again and click Enable.
8. Open a command prompt, and type ipconfig /all to check, whether the new MAC address has been changed. If the displayed physical address is still the same, your network card is probably incapable of changing this setting.
Here is the proof:
Here is the proof:
 |
| Changed mac address |
9. That’s all, enjoy your new spoofed mac address.
I hope you all like it…. If you have any queries ask me in form of comments…



No comments